You can manage computer and user resources within a System Center 2012 R2 Configuration Manager environment only when Configuration Manager has discovered these resources and assigned them to a site. In this post , you will learn about boundaries and boundary groups that help create logical network locations that contain discovered computers based upon IP addresses or Active Directory® sites.
You can use these boundary configurations for client site assignment and for helping clients find content from associated site systems. You also will learn about the discovery processes that you can use to identify computers, users, and the network infrastructure within your network environment. You then will learn about collections that support logical groupings of resources. You use these groupings for management tasks such as targeting software updates, managing applications, or deploying compliance settings to resources.
Additionally, you will learn to implement role-based administration by using security roles, security scopes, and collections. Role-based administration determines both the tasks that an administrative user can perform, and the objects and resources on which the user can perform those task
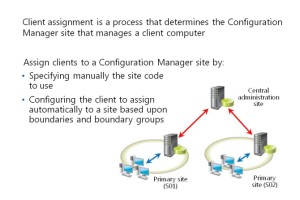
Overview of Client Assignment
Before you can use some Configuration Manager features to manage a computer resource, you
must install the client software on that computer, and the computer must join a primary site.
Site assignment is the process of a client joining a primary site, and you assign clients only to
primary sites. You cannot assign clients to a central administration site or a secondary site
What Is a Boundary?
A boundary is a network location that contains one or more devices that you want to manage or
resources that you want to provide to clients. Your network infrastructure is most likely
separated into several network locations, each of which contains network clients. Configuration
Manager can use each of these network locations to organize clients into boundaries, and you can define a boundary as one of the following types:
• IP subnet. You can use this boundary type to specify network locations based on individual
subnet IDs. You can be very specific about each network location. However, frequent IP subnet changes or additions require additional boundary administration, such as moving a site to another site manually.
• Active Directory site. A boundary based upon an Active Directory site is the easiest method for
maintaining network locations. Active Directory administrators create Active Directory sites, which typically represent distinct network locations. One main advantage for using Active Directory sites for Configuration Manager boundaries is that any subnet changes to the Active Directory sites are reflected within the boundaries automatically. However, one disadvantage is that you must rely on the proper configuration of the Active Directory sites. If the Active Directory administrator has not configured the site settings properly, you may have unmanaged clients within the improperly configured subnets or clients assigned to the wrong Configuration Manager site.
• IPv6 prefix. You can use this boundary type if your network infrastructure uses IP addresses based upon the Internet Protocol version 6 (IPv6) architecture. This supports the current and future operating systems that rely on this IP addressing method.
• IP address range. You can use this boundary type if you need to be very granular when specifying clients. You can use a range to specify a single client for testing purposes, or you can add a range of client addresses to represent any number of client devices. This method requires careful planning and administration to ensure that the IP ranges are not used as part of an IP subnet or another site’s Active Directory site-boundary configuration.
Configuration Manager boundaries are global, and each boundary definition is available from every primary site, secondary site, and the central administration site, within the hierarchy. A boundary itself does not enable client management at the network location. You have to add a boundary to a boundary group before the clients can be assigned to a specific site automatically or access content within a specific boundary.
Configure boundaries
To configure boundaries, open the Configuration Manager console, right-click the Boundaries node, and then select Create Boundary. The Create Boundary dialog box provides an option to select one of the four boundary types and configure the related settings, as necessary.
You also can manage boundaries with the following Configuration Manager cmdlets:
• New-CMBoundary. Use this cmdlet to create a new boundary.
• Get-CMBoundary. Use this cmdlet to view an existing boundary’s information.
• Set-CMBoundary. Use this cmdlet to alter an existing boundary’s properties.
• Remove-CMBoundary. Use this cmdlet to remove an existing boundary
What Is Resource Discovery?
Resource discovery is a process through which you can search a network for resources that you can use and manage with Configuration Manager. A resource is an object that is discovered by one of the available Configuration Manager discovery methods. During resource discovery, resource information can come from a variety of sources including Active Directory objects, such as users, groups, and computers; site systems; routers; printers; and other IP-addressable devices on your network. You can use the discovered resources to
create custom queries and organize resources into collections that you can use for management tasks, such as software deployments.
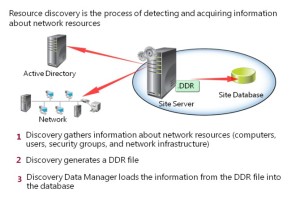
Resource discovery is a process through which you
can search a network for resources that you can use and manage with Configuration Manager.
Discovery data records
When Configuration Manager discovers resources, it creates discovery data records (DDRs) that it submits to the Configuration Manager database. Each generated file has a DDR extension, and the specific information that each record contains varies depending on the resource that Configuration Manager discovered and the discovery method it used. However, records can include data such as the NetBIOS name of a computer, IP address and IP subnet of a computer or device, operating system, and media access control (MAC) address.
The Discovery Data Manager component loads the discovered data from the DDR file into the site database. Depending on the configuration of the discovery method used, resource DDRs are regenerated periodically to update the discovery data and to verify that each resource is still a valid resource within the Configuration Manager site.
Note: If the primary site is connected to a central administration site, DDR records for
unknown resources are transferred to the central administration site by using file-based
replication and then entered into the database. Then, Microsoft SQL Server® database replication replicates the discovery information throughout the hierarchy’s primary sites. However, DDRs for known resources are processed at the primary site and are then replicated to the central administration site by using database replication. After a discovered resource becomes a client of a specific site, the discovery information is no longer replicated between other primary sites throughout the hierarchy.
If a resource’s discovery data is not updated within a specific amount of time, a site-maintenance task called Delete Aged Discovery Data will remove the resource’s data from the database. This task is, by default, configured to delete data older than 90 days. You can modify this site-maintenance task in the Administration workspace by expanding the Site Configuration node, clicking the Sites node, rightclicking the site name, and then clicking Site Maintenance.
Overview of Discovery Methods
Configuration Manager provides five configurable methods that you can use to discover network resources. Each of these methods returns a different set of discovered resources. Each of the discovery methods, except Heartbeat Discovery, is disabled by default.

Configuration Manager provides five configurable
methods that you can use to discover network
resources.